FACT Platform Overview
Framework for Analysis and Coordinated Trust
Overview
FACT is a powerful platform for correlating information from many sources about IT, ICS, IIoT, and IoT software supply chains.
It provides unprecedented visibility — right down into the very bits of the software — to prevent the installation of unsafe software in critical systems. FACT offers versatility, security, and powerful, AI-driven analysis:
- Available as a cloud product with private cloud and on-premises deployments available upon request
- Product-, platform-, operating system-, and vendor-agnostic
- Combines machine learning (ML), natural language processing (NLP), and binary analysis
- Offers proven security: the platform follows the AWS security best practices standard and has undergone extensive red team testing by AIS Infosec on behalf of the Department of Homeland Security
- Uses proven cryptographic technology that is known to be quantum-safe
- Easily integrates with existing company processes via a full-featured RESTful API
How It Works
aDolus addresses software supply chain risk by collecting information about software used in critical systems and "smart" devices from as many diverse sources as possible.
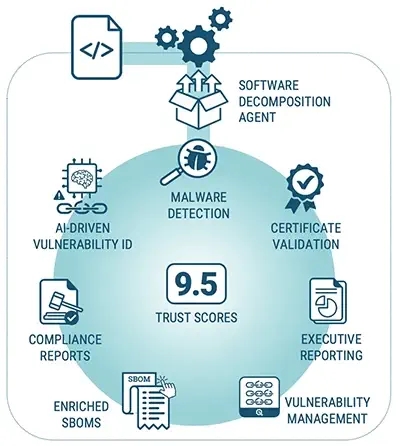
We then use artificial intelligence (AI) techniques to correlate that data and produce Trust Scores for software. ICS environments need a way to trust software and firmware that cannot be signed and FACT allows you to authenticate these unsignable files.
The Short Story
Companies that develop software or manufacture products containing firmware subscribe to the FACT service. They then submit samples of their software (or use our analysis agent in their development process) to generate a Software Bill of Materials (SBOM) for the product.
That SBOM is securely transferred to our platform where we analyze each software component and use AI to systematically search dozens of different company, product, vulnerability, and malware databases to see what is known about each component and the company that created it. We aggregate all this information into the FACT Trust Score and FACT Trustworthiness Report.
Companies that use these products can query FACT to validate new software, patches, and upgrades before installing them in critical equipment.
Let's get in touch so we can show you what FACT can do.
FACT in More Detail
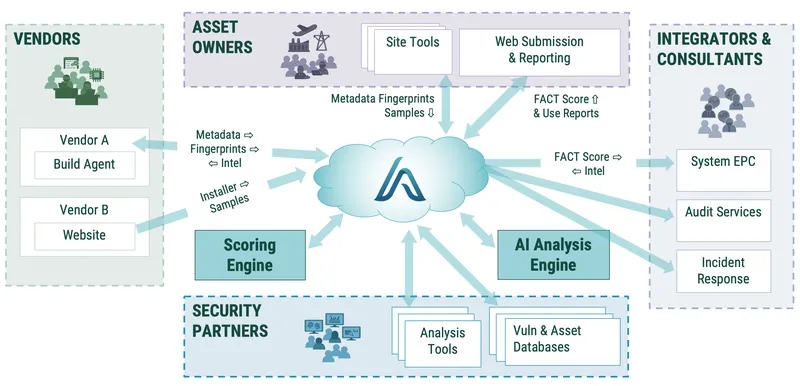
Vendors certified by aDolus generate SBOMs of their legitimate software and firmware via our automated agent within the secure perimeter of their software development process.
Alternately, they can send us their software and we generate the SBOMs using our servers. Either way, the SBOM or the software is transferred over an encrypted link to our FACT servers.
FACT verifies the authenticity of the vendor and stores the SBOM in a secure database, along with digital fingerprints, creating a repository of trusted artifacts. Using our AI technology, we then search public databases (like the National Vulnerability Database) and work with partners like ReFirm Labs and Nextron Systems to determine if any component in the SBOM contains vulnerabilities or malware. We also analyze the source and authenticity of each component through certificate analysis and services like SecurityScoreCard. We then provide a report to the vendor, allowing them to understand how their customers will experience their software and what security improvements might be advisable.
The asset owner's technical staff obtain firmware/software releases through their normal distribution channels (such as USBs or vendor websites). Prior to installing the firmware/software, the staff use the aDolus web client (or a local tool such as a file analyzer or network traffic analyzer) to generate their own digital fingerprint of the unverified firmware/software.
FACT compares the fingerprint of the unverified content against the certified digital fingerprints stored in the repository. It then provides a confidence and security rating of the unverified firmware/software and all its subcomponents. Based on this score, asset owner management can decide to approve or reject the firmware/software for use in their operations.
FACT also provides the management team with SBOMs and software risk reports and indicates where vulnerable packages may be deployed in their company.
In The End
If the two digital fingerprints match and the FACT confidence rating is high, the asset owner is assured that the firmware/software is valid, authorized by the provider, and secure.
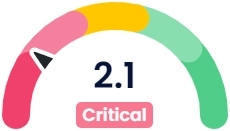
If the FACT confidence rating is low, the asset owner is alerted that the software may expose company operations to security risks. If the fingerprints don't match, then the asset owner has been alerted to non-compliant content before installing it in critical equipment.